DroidAnalytics: A Signature Based Analytic System to Collect, Extract, Analyze and Associate Android Malware
Min Zheng, Mingshen Sun, and John C.S. Lui
The 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, TrustCom '13.
Availability:
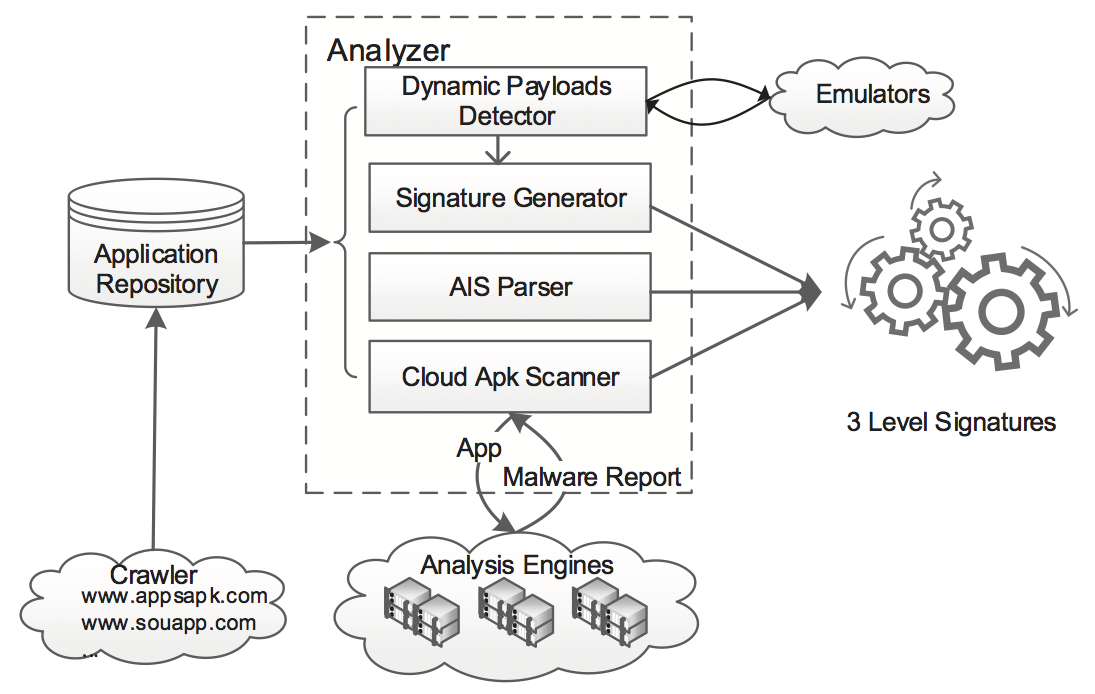
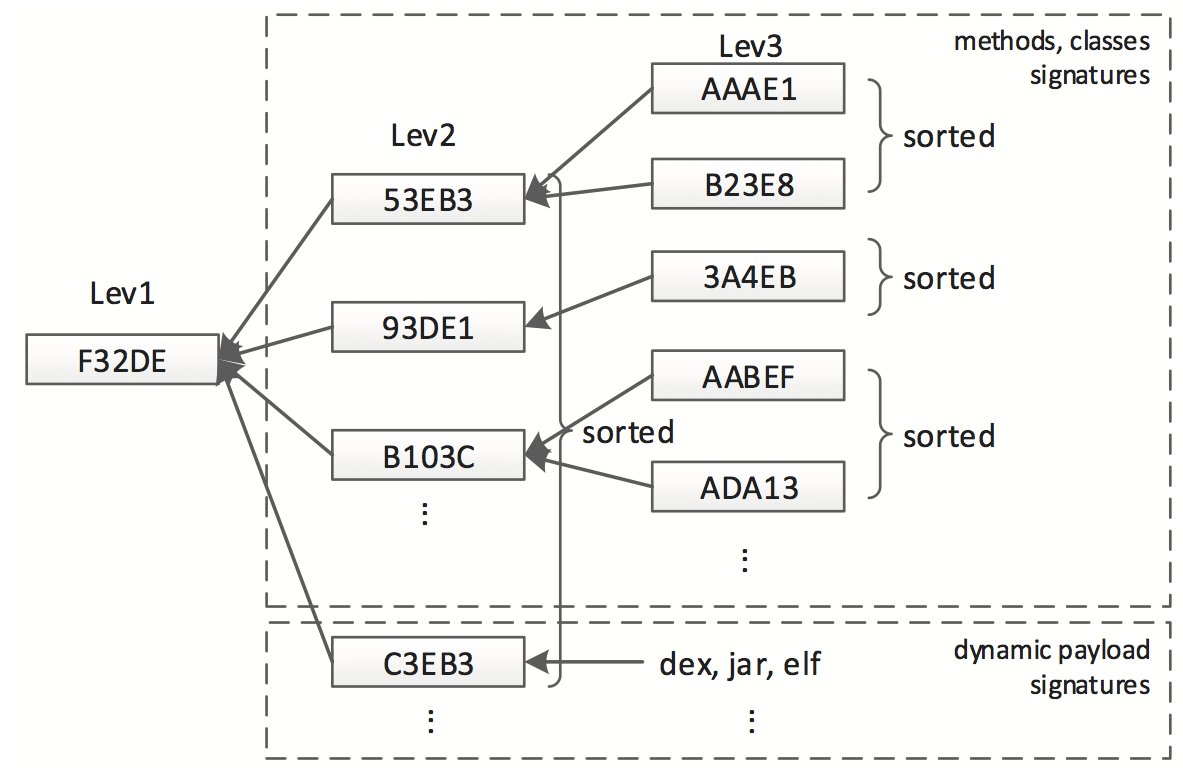
Abstract. Smartphones and mobile devices are rapidly becoming indispensable devices for many users. Unfortunately, they also become fertile grounds for hackers to deploy malware. There is an urgent need to have a "security analytic & forensic system" which can facilitate analysts to examine, dissect, associate and correlate large number of mobile apps. An effective analytic system needs to address the following questions: How to automatically collect and manage a high volume of mobile malware? How to analyze a zero-day suspicious app, and compare or associate it with existing malware families in the database? How to reveal similar malicious logic in various malware, and to quickly identify the new malicious code segment? In this paper, we present the design and implementation of DroidAnalytics, a signature based analytic system to automatically collect, manage, analyze and extract android malware. The system facilitates analysts to retrieve, associate and reveal malicious logics at the "opcode level". We demonstrate the efficacy of DroidAnalytics using 150,368 Android apps, and successfully determine 2,475 Android malware from 102 different families, with 327 of them being zero-day malware samples from six different families. In addition, the experiments show our methodology has a 95.1% heuristic detection rate and saves 96.5% storage size.
BibTeX Record:
@inproceedings{zheng2013droid,
title={DroidAnalytics: A Signature-based Analytic System to Collect, Extract, Analyze and Associate Android Malware},
author={Zheng, Min and Sun, Mingshen and Lui, John C.S.},
booktitle={Proceedings of the 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications},
series = {TrustCom '13},
year={2013},
}